The best defense is to be prepared
Securing company data and intelligence is one of the top concerns of a thriving business like yours. As a business owner, you need to be prepared for everything that may affect your business. Antivirus software might help, but is not guaranteed to solve the root cause of the issue. Hackers are constantly coming up with ways to get around antivirus software. EMSCO Solutions can help you. We offer our extensive experience in handling and removing CryptoLocker or any ransomware computer infections. Our technical experts are capable of prevention, retrieving the data, and cleaning the infection caused by CryptoLocker with minimal disruption from your business operations.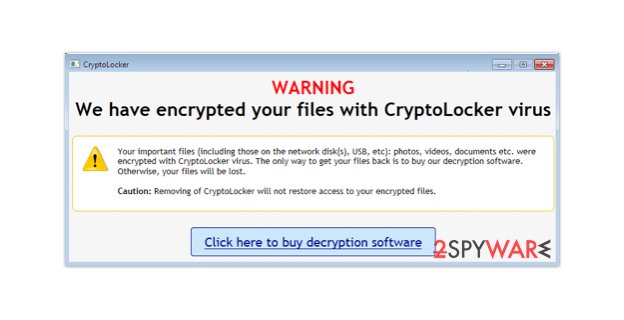
A screenshot from one of our clients that was hit by Cryptolocker attack, that we have resolved.
More about CryptoLocker:
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late-May 2014. The attack utilized a trojan that targeted computers running Microsoft Windows, and was believed to have first been posted to the Internet on 5 September 2013. It propagated via infected email attachments, and via an existing Gameover ZeuS botnet; when activated, the malware encrypts certain types of files stored on local and mounted network drives using RSA public-key cryptography, with the private key stored only on the malware's control servers. The malware then displays a message which offers to decrypt the data if a payment (through either bitcoin or a pre-paid cash voucher) is made by a stated deadline, and it will threaten to delete the private key if the deadline passes. If the deadline is not met, the malware offered to decrypt data via an online service provided by the malware's operators, for a significantly higher price in bitcoin. There is no guarantee that payment will release the encrypted content. -WikipediaThe CryptoLocker ransomware targets all versions of Windows including Windows 7, Windows 8 and Windows 10. Files targetted by this Cryptolocker attack are the following.
.sql, .mp4, .7z, .rar, .m4a, .wma, .avi, .wmv, .csv, .d3dbsp, .zip, .sie, .sum, .ibank, .t13, .t12, .qdf, .gdb, .tax, .pkpass, .bc6, .bc7, .bkp, .qic, .bkf, .sidn, .sidd, .mddata, .itl, .itdb, .icxs, .hvpl, .hplg, .hkdb, .mdbackup, .syncdb, .gho, .cas, .svg, .map, .wmo, .itm, .sb, .fos, .mov, .vdf, .ztmp, .sis, .sid, .ncf, .menu, .layout, .dmp, .blob, .esm, .vcf, .vtf, .dazip, .fpk, .mlx, .kf, .iwd, .vpk, .tor, .psk, .rim, .w3x, .fsh, .ntl, .arch00, .lvl, .snx, .cfr, .ff, .vpp_pc, .lrf, .m2, .mcmeta, .vfs0, .mpqge, .kdb, .db0, .dba, .rofl, .hkx, .bar, .upk, .das, .iwi, .litemod, .asset, .forge, .ltx, .bsa, .apk, .re4, .sav, .lbf, .slm, .bik, .epk, .rgss3a, .pak, .big, wallet, .wotreplay, .xxx, .desc, .py, .m3u, .flv, .js, .css, .rb, .png, .jpeg, .txt, .p7c, .p7b, .p12, .pfx, .pem, .crt, .cer, .der, .x3f, .srw, .pef, .ptx, .r3d, .rw2, .rwl, .raw, .raf, .orf, .nrw, .mrwref, .mef, .erf, .kdc, .dcr, .cr2, .crw, .bay, .sr2, .srf, .arw, .3fr, .dng, .jpe, .jpg, .cdr, .indd, .ai, .eps, .pdf, .pdd, .psd, .dbf, .mdf, .wb2, .rtf, .wpd, .dxg, .xf, .dwg, .pst, .accdb, .mdb, .pptm, .pptx, .ppt, .xlk, .xlsb, .xlsm, .xlsx, .xls, .wps, .docm, .docx, .doc, .odb, .odc, .odm, .odp, .ods, .odt
To learn more about how we can help you stay safe from CryptoLocker ransomware (or remove it if you have already been infected), call us today at 405-813-4455 or fill out the the form to have us contact you.

You must be logged in to post a comment.